OAuth Token Expiry Challenges in Power BI Integration with Starburst Enterprise
Hi Team,
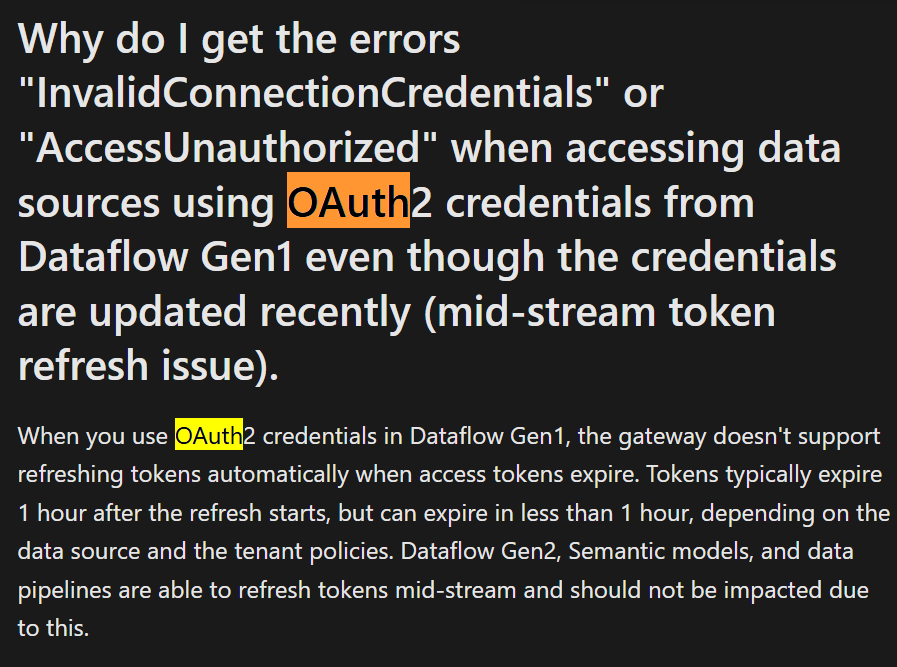
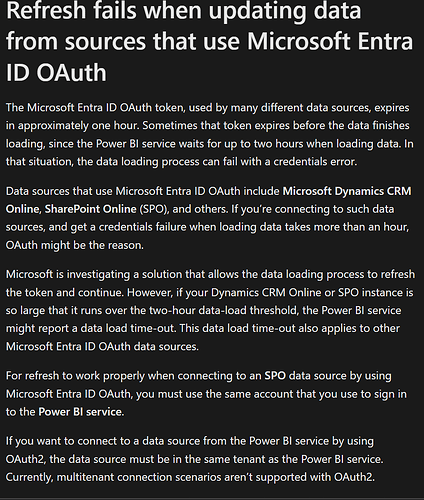
When using Starburst Enterprise with OAuth2 authentication, we face a recurring issue by design, the OAuth token expires after a short duration (typically 1 hour), and there is no built-in token renewal mechanism within Power BI.
This becomes especially problematic in two scenarios:
-
Power BI Desktop / Service Usage
In both Power BI Desktop and SaaS environments, the session dies after the token expires.
This interrupts user workflows, especially during development or heavy report use. -
Scheduled Report Refresh via Power BI Gateway
On Power BI Service, when we configure scheduled refresh using an on-prem Data Gateway, the refresh fails due to token expiration. Currently, there’s no automated way to reauthenticate or renew the token, making it infeasible to run unattended report refresh jobs.
This limitation blocks enterprise-grade reporting automation using Starburst as a data source which is counterproductive, especially when the platform is pitched as enterprise-ready.
Root Cause (as we understand)
The Starburst-Power BI connector is a custom connector, built using Power Query SDK, not a native Microsoft-certified connector. While this gives flexibility, it seems to lack advanced integration for token renewal or secure credential storage compatible with Power BI Service.
Our Concern
We’ve raised this with your Support Team and Customer Success Engineers, but the topic often gets sidestepped, citing known limitations or suggesting we use another BI tool.
But for users heavily invested in Power BI, this is a serious roadblock.
If this issue is not addressed transparently, it raises questions on how well Starburst integrates into real-world enterprise analytics stacks where automation, scheduling, and unattended execution are must-haves.
A Few Asks:
- Could your team publish a transparent guide or blog post on this topic? Even if it’s a known gap, openness goes a long way especially when competitors are already discussing these issues in public forums.
- Is there a roadmap or workaround in progress for automated token renewal or Service Principal-style auth with Power BI Gateway? ( I’ve noticed there’s another Starburst connector that uses Entra ID (Azure AD) for authentication, but surprisingly, your support team isn’t fully aware of the settings required for it. This raises a few concerns.
If you’re stating that Starburst integrates with Power BI, then naturally, your team should be well-versed with the configuration steps especially for an enterprise-grade connector. When such questions are raised by users, the response shouldn’t be vague or uncertain.
Also, if this integration was part of your alpha or internal testing, then how exactly was it tested? What settings were used? Was Entra ID authentication part of those test cases? It’s important that this clarity is shared otherwise, the claim of Power BI integration feels incomplete.
A proper configuration guide or shared test insights would be very helpful for all enterprise users trying to make this work in real-world reporting pipelines.)
- Can Starburst collaborate with Microsoft to push this into the certified connector roadmap even if limited to Enterprise editions?
This is a critical feature for production-grade usage of Starburst in modern data stack environments. We appreciate the innovation your team is building but support for major BI ecosystems like Power BI is essential for enterprise adoption.
Looking forward to a response or even better, a technical discussion on this topic.
Thanks,
Thara
(On behalf of many engineering teams exploring Starburst for analytics reporting)